Android逆向之2-優雅攔截sqlcipher sqlite數據庫密碼
《Android逆向之2-優雅攔截sqlcipher sqlite數據庫密碼》要點:
本文介紹了Android逆向之2-優雅攔截sqlcipher sqlite數據庫密碼,希望對您有用。如果有疑問,可以聯系我們。
在你逆向分析**app時,分析分析其數據存儲結構絕對是事倍功倍.
下面是我在hook 微信sqlite暗碼的分享
知識準備
1:懂的利用xposed框架或Cydia框架hook技術
2 :jadx工具(定位分析工具)
static public void wechatOpenDatabase(String wechatVersionName, final XC_LoadPackage.LoadPackageParam lpparam) {
/**
*調用生成SQLiteDatabase 重要入口
* //主要第3個參數是sqlite的暗碼
public static SQLiteDatabase openDatabase(String paramString1, LockedDevice paramLockedDevice, String paramString2, Arithmetic paramArithmetic, CursorFactory paramCursorFactory, int paramInt1, DatabaseErrorHandler paramDatabaseErrorHandler, boolean paramBoolean, int paramInt2)
{
SQLiteDatabase localSQLiteDatabase = new SQLiteDatabase(paramString1, paramInt1, paramCursorFactory, paramDatabaseErrorHandler);
localSQLiteDatabase.open(paramLockedDevice, paramString2, paramArithmetic, paramBoolean, paramInt2);
return localSQLiteDatabase;
}
*/
try {
Class clazzPalue3= null;
if (wechatVersionName.equals("6.3.13.56_r238e8af")){
clazzPalue3 = String.class;
}else {
clazzPalue3 = byte[].class;
}
XposedHelpers.findAndHookMethod(PluginsConfigWechatSqlite.WECHAT_SQLiteDatabase_CLASSE, lpparam.classLoader, "openDatabase",
String.class, //sqlite 數據庫文件全路徑如:/data/data/com.tencent.mm/MicroMsg/71daf7e10a38aa48ee8bad199dde232a/EnMicroMsg.db
lpparam.classLoader.loadClass(PluginsConfigWechatSqlite.WECHAT_SQLiteDatabase_CLASSE+"$LockedDevice"),
clazzPalue3,//byte[].class,//String.class, //6.3.13版本string.class6.3.31是byte[].class sqlite數據庫的暗碼如21e8906
lpparam.classLoader.loadClass(PluginsConfigWechatSqlite.WECHAT_SQLiteDatabase_CLASSE+"$Arithmetic"),
lpparam.classLoader.loadClass(PluginsConfigWechatSqlite.WECHAT_SQLiteDatabase_CLASSE+"$CursorFactory"),
int.class,
lpparam.classLoader.loadClass(PluginsConfigWechatSqlite.WECHAT_SQLiteDatabase_3Level_CLASSE+".DatabaseErrorHandler"),
boolean.class,
int.class,
new XC_MethodHook() {
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
String strSqliteDatabaseFilePaht= (String) param.args[0];
//if (strSqliteDatabaseFilePaht.endsWith("EnMicroMsg.db") && EnMicroMsgSQLiteDatabaseObject ==null) { //獲取EnMicroMsg對應的SQLiteDatabase
if (strSqliteDatabaseFilePaht.endsWith("EnMicroMsg.db")) { //獲取EnMicroMsg對應的SQLiteDatabase
EnMicroMsgSQLiteDatabaseObject = param.getResult();
System.out.println("SQLiteDatabaseObject的類名:"+ EnMicroMsgSQLiteDatabaseObject.getClass().getName());
}
}
@Override
protected void beforeHookedMethod(MethodHookParam param) throws Throwable {
//SQLiteDatabase db = SQLiteDatabase openDatabase(String path, SQLiteDatabase.CursorFactory factory, int flags)
String mm ="";
if (param.args[2] !=null){
String str= param.args[2].getClass().getName();
if (str.equals("[B")){
byte[] mmbytes = (byte[]) param.args[2];
mm = new String(mmbytes,"UTF-8");
}else if (str.equals("java.lang.String")) {
mm =""+param.args[2];
}
}
//Log.i(TAG,"openDatabase String 0參數sqlite全路徑和暗碼: " +param.args[0]+"參數sqlite暗碼:" +param.args[2].toString());
Log.i(TAG,"openDatabase String 0參數sqlite全路徑和暗碼: " +param.args[0]+"參數sqlite暗碼:" +mm);
}
});
} catch (ClassNotFoundException e) {
e.printStackTrace();
}
}
jadx工具分析定位在com.tencent.mmdb.database.SQLiteDatabase

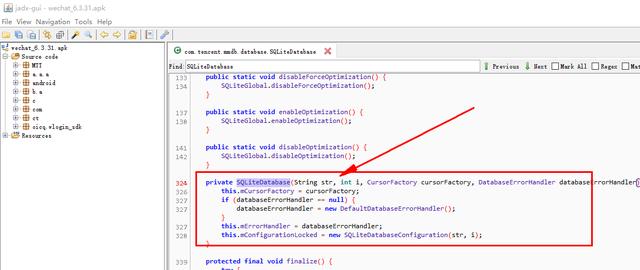
啟動**發現微信啟動時同時打開的數據庫有
最后感謝今日頭條提供的分享平臺,你覺得有用可以收藏便利以后查閱.
分享是一種美德,牽手是一種生活方式.
歡迎參與《Android逆向之2-優雅攔截sqlcipher sqlite數據庫密碼》討論,分享您的想法,維易PHP學院為您提供專業教程。
